Critical Facebook security flaw allows hackers to log into multiple Facebook accounts
How to hack Facebook is the most popular search term on Google but a few go past learning to the actual hacking. However, one California-based hacker tried something similar. During his researcher he discovered a big security hole in Facebook’s password reset mechanism which allowed him to hack into anyone’s Facebook profile.
California based Gurkirat Singh discovered a way to gain access to anyone’s Facebook profile using a security flaw in the social networking giant’s password reset mechanism. The social networking giant uses an algorithm that generates a random 6-digit passcode ‒ that’s 10⁶ = 1,000,000 possible combinations.
“That could possibly mean that if 1 million people request a password within a short amount of time such that no one uses their code to reset the password, then 1,000,0001 person to request a code will get a passcode that someone from the batch has already been assigned,” Gurkirat explains in a blog post.
According to him, Facebook needs to store duplicate codes for multiple users if more than 1,000,000 users request a password reset. This means that more than two people have the same passcode. To use this for his purpose, Gurkirat Singh devised a way to send in 2 million password change requests to Facebook.Doesn't get any simpler! #Hacking #Facebookhttps://medium.com/@gurkiratsingh/how-i-could-have-hacked-multiple-facebook-accounts-d9d335188d9b#.5o8oq5s15 …
How I Could Have Hacked Multiple Facebook Accounts
Let’s get into the nitty-gritty. The only way you can reset your password on Facebook (if you’ve forgotten one) is through entering a 6…
hackernoon.com
Since Facebook IDs are 15-digit long, Singh used 1,00,000,000,000,000 and made queries to Facebook Graph API to see which IDs were valid. This can only be done through authorized apps, and once a match is found, you can enter the ID in the URL like www.facebook.com/[ID]. The URL then automatically changes the ID to the username. This data was compiled into a JSON by Singh.
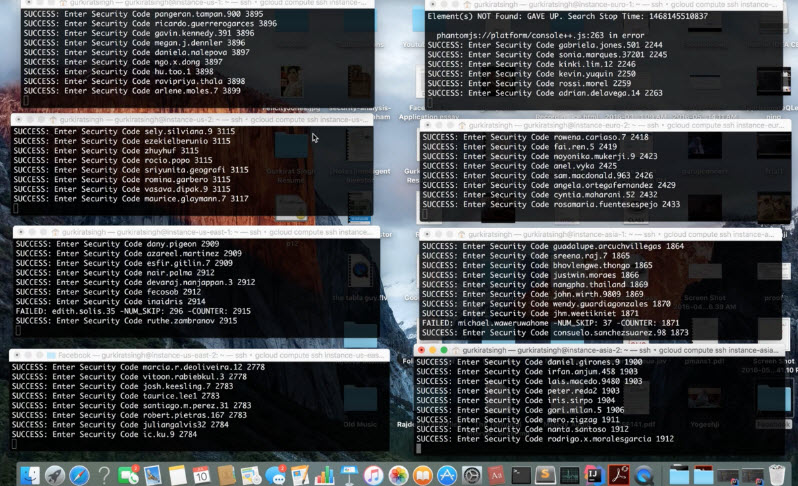
To handle the problem of IP changing, Gurkirat Singh simply used a proxy server that listened to HTTP Requests and then assigned a random IP address to each request. He used a multithreaded script to simulate user behaviour when a passcode is required. The script requests a passcode to every user in the JSON file created earlier. Then the scripts were run to make the requests. It looked like this:


No comments:
Post a Comment