Snow currently has around 80 million downloads, and it is adding around 10 million more each month, according to the source. That growth has also encouraged acquisition interest from Tencent — the maker of blockbuster chat app WeChat — Alibaba and others, TechCrunch understands.
“It’s true that Snow is receiving love calls from various companies,” a representative from Naver told us in a statement. Despite acknowledging outside interest, Naver did not name Snow’s would-be suitors.
Facebook did not respond to requests for comment.
The app first grabbed attention in the summer when it raced up Android and iOS app store rankings in Korea, Japan and China, collecting some 30 million downloads. A feature story from The New York Times in July, which explained that Snow and Naver were exploiting Snapchat’s apparent lack of interest in Asia, only served to heighten awareness of the app.
Sometime after that story, Facebook CEO Mark Zuckerberg got wind of Snow and contacted Naver Chairman Hae-Jin Lee over the phone with an offer to acquire it. Naver saw Line raise over $1 billion in a dual Japan-U.S. IPO in July of this year, and Lee rejected Facebook’s overtures because he believes Snow has the potential to become a similar success.
Indeed, Naver strengthened ties between the two services in September when Line made a $45 million investment in Snow that gave the social app a valuation of $180 million — not bad for a one-year-old project. With Line struggling to grow its userbase outside of its largest markets of Japan, Thailand and Taiwan, Snow is viewed as a key ally that could help the chat app broaden its appeal in more parts of Asia.
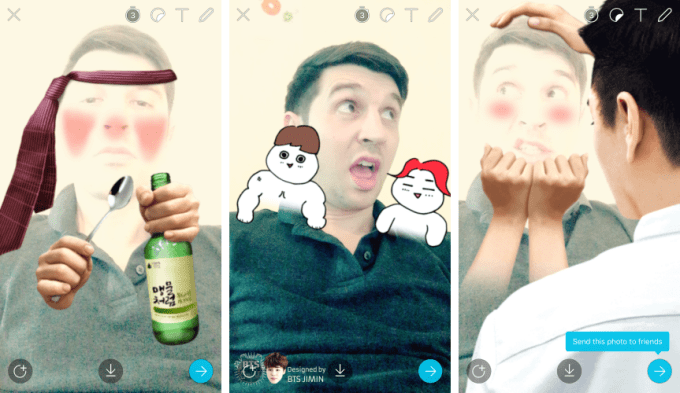
While it is easy to label Snow as a Snapchat clone, the app does have some differentiated features.
For one thing, Naver has worked hard to localize the service in markets, much the same way as it did with Line when the chat app emerged in 2011-2012. Most notably, it is working with celebrities in Korea and Japan, where it sees the most traction and potential, to feature their stories prominently inside the app alongside live streams, too. That helps encourage users back into the app for more reasons than simply to message their friends, while it also may unlock monetize options in the future.
The app itself has over 36 filters and more than 200 masks, offering considerably more customization options than Snapchat — a move that is in line with appealing to its core audience in Asia. Some options include filters for both images and videos that involve celebrities, cartoon characters, fairies and even one scene as a drunken ‘salary man’ making a toast.
Snapchat — now just ‘Snap’ — is widely reported to be gearing up for an IPO next year thatcould value the company at around $25 billion. The latest suggestion is that it could raise $4 billion from a listing.
Those figures certainly vindicate CEO Evan Spiegel’s decision to reject a $3 billion bid from Facebook three years ago — even if conventional wisdom at the time suggested he was making a mistake.
It is still early days for Snow, and it remains to be seen whether this will be another app that Facebook will rue missing out on over time.
For now, Facebook is trying to turn its own properties into Snapchat-like competitors using heavy doses of ‘product inspiration’.
Instagram Stories, a feature that the company admits is inspired by Snapchat, reached a very respectable 100 million users within two months, while Facebook has launched smaller projects that include a social video app that’s just for teens, a Snapchat-like camera feature, and a fairly blatant Snapchat clone that is being tested in Poland.








